Previously I have setup qemu for testing by using the quick how-to at the taosecurity blog
here. Everything is going well and I'm pretty satisfied to run qemu for my pre-deployment testing. However the setup won't allow me to connect to the Virtual Machine remotely by using localhost, which means that I can only interact with qemu VM by login to another machine and connect back to qemu VM. This is not a big problem anyway but it kills my need of running everything with my standalone notebook only.
After going through the man page of if_bridge, I decided to create bridge interface using it instead of the one mentioned in bridge man page. Both are different and you can read it anyway by just run man if_bridge and man bridge. With that I have successfully connect to qemu VM with localhost. All I need is just run my VM with the command,
Then create the bridge interface and adding the physical interface - bge0 and the pseudo interface - tap0 to the bridge interface.
shell>ifconfig bridge0 create shell>ifconfig bridge0 addm bge0 addm tap0You need to assign the IP to the bridge interface if you want to have the VM connecting to internet, and don't forget to delete the ip configuration of the bge0 interface.
shell>ifconfig bridge0 inet 192.168.0.199 \ netmask 255.255.255.0 up shell>ifconfig bge0 inet deleteNow you may have the VM in the same LAN is the bridge interface, just configure your network interface in the VM to be something within range 192.168.0./24 will do. The NIC variable in my OpenBSD VM is ne3, just run ifconfig utility to configure the IP address will do.
Remember I have told that I'm creating the sguil qemu image, currently it is in the progress and I named it as NSM.img(OpenBSD VM), this is working properly with single NIC. I can ping each other and interact with VM perfectly fine.
But is this what I want? I remember I used to create multiple NICs in my VMware, I crawled the qemu man page and found that I can actually create multiple NICs by running,
shell>qemu -boot c -hda /nsm/i-VMimages/NSM.img \ -net nic -net tap -net nic -net tapOnce the VM is started, I found ne3 and ne4 network interfaces in my VM, I thought that everything is going as expected, I add IP address 192.168.0.123 to ne3 and 192.168.0.124 to ne4, then I start to ping 192.168.0.123, now havocs started where I have tons of DUPLICATE ping packets. If this is the case that would be bad since I can't setup my VM with multiple NICs.
Since I'm not a give up type, I crawled against the qemu manual page. I found that I can actually create the NICs with different vlan setting. Thus I might give it a try, I run the commands,
shell>qemu -boot c -hda /nsm/i-VMimages/NSM.img \ -net nic -net tap,vlan=0,ifname=0 \ -net nic -net tap,vlan=1,ifname=1Without making any assumption that it works, I start to ping 192.168.0.123, and this time everything goes fine and I don't see any problem, this is what I really want and I got it running this time. Now I can start tinkering with my NSM setup on qemu image. With the correct configuration of gateway and dns server, both my localhost and VM can connect to the internet. Check the screenshots below and look at the interface configuration and the ping result of my VM to localhost and internet, it just works!!!!!
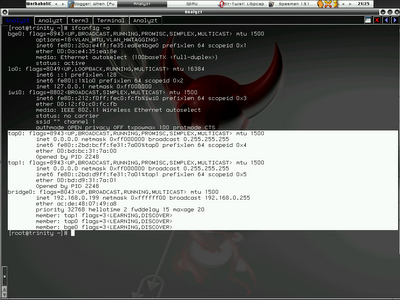
My network interface configuration
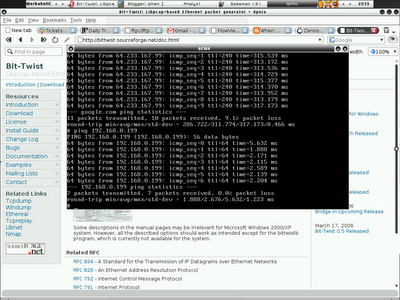
VM pinging localhost and internet
If you don't want to use qemu anymore, and would like to delete the pseudo interfacessuch as tap and bridge interface, normally you don't have to do the ifconfig NIC destroy, you are better of doing this - unload the pseudo interfaces module,
shell>kldstatId Refs Address Size Name
1 19 0xc0400000 6a29c0 kernel
2 1 0xc0aa3000 5f60 snd_ich.ko
3 2 0xc0aa9000 22b88 sound.ko
4 1 0xc0acc000 58554 acpi.ko
5 1 0xc4ebd000 9000 if_iwi.ko
6 1 0xc4fe1000 16000 linux.ko
7 1 0xc5267000 5000 i915.ko
8 1 0xc526c000 e000 drm.ko
10 1 0xc5a69000 4000 if_tap.ko
11 1 0xc5a41000 8000 if_bridge.ko
shell>kldunload if_tap shell>kldunload if_bridgeThat's the right way of deleting pseudo interface instead of using ifconfig. On the other hand, I have found the mail thread where people are asking of problem when creating tap interface. Normally you just need to do this to avoid the unwanted error.
shell>kldload if_tap shell>cat /dev/null > /dev/tap0
I just point out here in case this helps when people googling for answer :P
Though it is not as user friendly as VMware, I will still stick with qemu for the time being. I think the more I use qemu, the more I can do with it in practical environment.
Note: I will add this write-up to my handbook, for the section - Building cheapest testing lab environment.