This looks like interesting dual ports network adapter with bypass function, more information ->
http://www.portwell.com/products/detail.asp?CUSTCHAR1=ABN-192
If you know where can get this in Malaysia, please do let me know.
Tuesday, December 23, 2008
Saturday, December 20, 2008
NIDS: Administration, Management & Provisioning
We often find many resources that discuss about NIDS technologies, and how can you setup one, however things that are really missed out there(even in the internet) should be the following.
If you are managing tons of Network Intrusion Detection systems(NIDS), for tons I mean more than 50, I would like to hear from you about -
1. What tools do you use to manage all the NIDS, and why you choose them over others?
- For example ssh, however I would like to know more about tools you use to manage massive NIDS instead of one, and the reason you choose it.
2. How do you perform efficient administration securely? For examples,
- System changes/updates
- NIDS tools' changes/updates
- NIDS rules' changes/updates
- NIDS Configuration files' changes/updates
- NIDS Policies' changes/updates
3. Which method you like to use in order to manage them, and why? For example,
- Server pushes rules update to all the sensors(Push)
- Sensors pull the rules update from server(Pull)
3. NIDS health monitoring and self-healing
- I'm talking about something like this, if the system is in incosistent state, operators will be notified. If certain process die, it should recover by itself.
I consider NIDS as critical system and it should be managed wisely to prevent misconfiguration, downtime and so forth. Therefore we should have solid answers for the questions above if we are going for massive NIDS implementation and deployment.
Any in sight or valuable thoughts to share are welcomed!
Peace ;]
If you are managing tons of Network Intrusion Detection systems(NIDS), for tons I mean more than 50, I would like to hear from you about -
1. What tools do you use to manage all the NIDS, and why you choose them over others?
- For example ssh, however I would like to know more about tools you use to manage massive NIDS instead of one, and the reason you choose it.
2. How do you perform efficient administration securely? For examples,
- System changes/updates
- NIDS tools' changes/updates
- NIDS rules' changes/updates
- NIDS Configuration files' changes/updates
- NIDS Policies' changes/updates
3. Which method you like to use in order to manage them, and why? For example,
- Server pushes rules update to all the sensors(Push)
- Sensors pull the rules update from server(Pull)
3. NIDS health monitoring and self-healing
- I'm talking about something like this, if the system is in incosistent state, operators will be notified. If certain process die, it should recover by itself.
I consider NIDS as critical system and it should be managed wisely to prevent misconfiguration, downtime and so forth. Therefore we should have solid answers for the questions above if we are going for massive NIDS implementation and deployment.
Any in sight or valuable thoughts to share are welcomed!
Peace ;]
Thursday, December 18, 2008
*nixes Backup Solution
Sunday, December 14, 2008
FreeBSD ZFS
I have been listening people talking about ZFS, and it is ported to FreeBSD, I don't play with it until today.
It does seem that FreeBSD is getting solarish, ZFS, Dtrace and what else. Anyway here's simple screenshot of mine with ZFS setup -
It does seem that FreeBSD is getting solarish, ZFS, Dtrace and what else. Anyway here's simple screenshot of mine with ZFS setup -

I may spend more time playing with it, if you are interested in ZFS on FreeBSD, you should check out -
http://wiki.freebsd.org/ZFS
By the way, FreeBSD 7.1 RC1 is out, grab it while it's hot!
http://wiki.freebsd.org/ZFS
By the way, FreeBSD 7.1 RC1 is out, grab it while it's hot!
Cheers ;]
Saturday, December 13, 2008
Anonymous Troll
I have previously blogged about my experience in Singapore Govware here, however I don't know I get such interesting comment until I was told by a friend who read it. The comment is written as following -
--------------------------------------------------------------
Anonymous said ....
With all due respect to you and your great work with hex and what not, I'd like to rant a bit. I know its belated, but here goes :)
Sometimes security is not about you 'teaching' people what to do with your l337 NSM toolkit. It is normal for security conferences/events to be a closed door affair or by invitation only. I bet there were some concerns by some parties that you're blackhats/can't_be_trusted/not-really-security-analyst whom they can share information with. So its better late than never to kick you out. The level or kind of stuff you and other l337 friends write at security.org.my also don't help I think.
So get real, be trusted, and stop associating yourself with ppl whose deep insights on security are only by taking screenshots at defacements or error messages, blowing them out of porportion, make kidd1e5 happy and then sell a training program! So don't be disheartened at being kicked out at a per invite only program.
-----------------------------------------------------------
I don't really want to argue anything here, my point here is if you don't know me, don't justify me with your narrow minded like you know me very well, and stop acting like anonymous coward.
--------------------------------------------------------------
Anonymous said ....
With all due respect to you and your great work with hex and what not, I'd like to rant a bit. I know its belated, but here goes :)
Sometimes security is not about you 'teaching' people what to do with your l337 NSM toolkit. It is normal for security conferences/events to be a closed door affair or by invitation only. I bet there were some concerns by some parties that you're blackhats/can't_be_trusted/not-really-security-analyst whom they can share information with. So its better late than never to kick you out. The level or kind of stuff you and other l337 friends write at security.org.my also don't help I think.
So get real, be trusted, and stop associating yourself with ppl whose deep insights on security are only by taking screenshots at defacements or error messages, blowing them out of porportion, make kidd1e5 happy and then sell a training program! So don't be disheartened at being kicked out at a per invite only program.
-----------------------------------------------------------
I don't really want to argue anything here, my point here is if you don't know me, don't justify me with your narrow minded like you know me very well, and stop acting like anonymous coward.
Peace ;]
What Am I Doing?
I hardly blog these days, and have been busy with current works plus my own fun research. It's about the end of year 2008 and I figure life is more challenging when I'm getting older.
raWPacket is currently in the state of "slowing down" or you can call it slacking, so we will restart our engine next year(2009). Hopefully we can get many interesting projects done in coming year, some are on the way!
It's been couple of months working for GE now, thanks to my friend - Richard Bejtlich for the opportunity, faithfully. For the other guys I'm working with, you guys are always rocking!
For my own research, lets keep it secret for now, it will be revealed soon.
raWPacket is currently in the state of "slowing down" or you can call it slacking, so we will restart our engine next year(2009). Hopefully we can get many interesting projects done in coming year, some are on the way!
It's been couple of months working for GE now, thanks to my friend - Richard Bejtlich for the opportunity, faithfully. For the other guys I'm working with, you guys are always rocking!
For my own research, lets keep it secret for now, it will be revealed soon.
Cheers ;]
Monday, December 01, 2008
Drunken Monkey: Running Network Miner with Wine
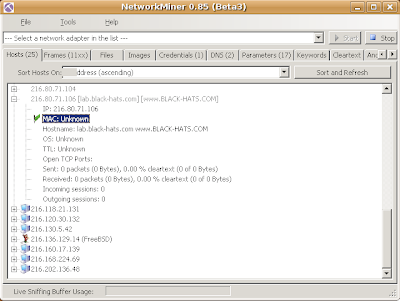
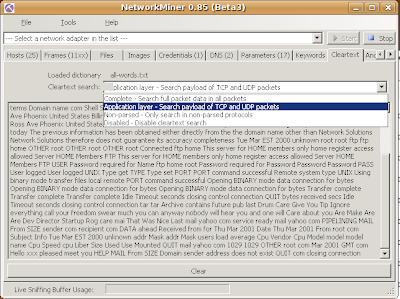
Network-Based Forensics is emerging now, we are seeing more and more NBF tools in active development now, one of the decent NBF tool I would like to mention here is NetworkMiner which is developed by Erik Hjelmvik. NetworkMiner is developed using .net framework, therefore it has Windows version only, I will show you how you can get it running using Wine on *nix based OS especially Ubuntu Linux.
Installing Wine -
shell>sudo apt-get install wine wine-dev cabextract
Configure Wine -
shell>winecfg
In Application tab, change windows version to Windows 2000
shell>wget http://kegel.com/wine/winetricks
Install cofefronts and .net framework 2.0 -
shell>sh winetricks corefonts dotnet20
Download NetworkMiner -
Unzip it and run -
shell>wine NetworkMiner.exe
Here you go -
Installing Wine -
shell>sudo apt-get install wine wine-dev cabextract
Configure Wine -
shell>winecfg
In Application tab, change windows version to Windows 2000
shell>wget http://kegel.com/wine/winetricks
Install cofefronts and .net framework 2.0 -
shell>sh winetricks corefonts dotnet20
Download NetworkMiner -
shell>wget \
http://sourceforge.net/project/showfiles.php?group_id=189429
http://sourceforge.net/project/showfiles.php?group_id=189429
Unzip it and run -
shell>wine NetworkMiner.exe
Here you go -
Cheers (;])
Subscribe to:
Comments (Atom)