There's one of the project in
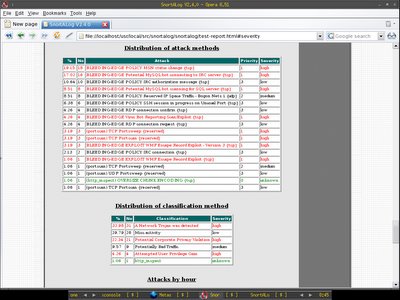
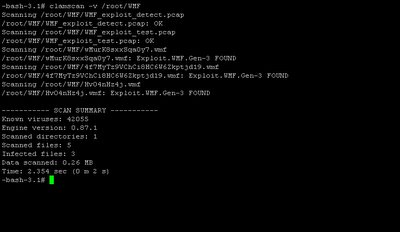
Bleedingsnort that I would like to try out - Snort-ClamAV, with the ClamAV preprocessors, it can scan the data stream that travelling across the wire for viruses, maybe it is not as useful as it seems since nowadays most of the host has personal antivirus software deployed, however it would notify and may drop the viruses/worms before reaching your client host in the network. Here's how I get Snort-ClamAV to work on OpenBSD current.
shell>groupadd clamav
shell>useradd -g clamav -d /home/clamav -s /bin/false -c "Clam Antivirus" clamav
shell>cd /usr/local/src
shell>wget http://jaist.dl.sourceforge.net/sourceforge/clamav/
clamav-0.87.1.tar.gz
shell>tar xzf clamav-0.87.1.tar.gz
shell>clamav-0.87.1
shell>./configure --prefix=/usr/local/clamav --sysconfdir=/usr/local/clamav/etc --disable-pthreads --disable-clamuko
shell>make && make install
Installing Snort-ClamAV preprocessorcd /usr/local/src
shell>wget http://www.bleedingsnort.com/cgi-bin/viewcvs.cgi/
root.tar.gz?root=Snort-Clamav&view=tar
shell>wget http://www.snort.org/dl/current/snort-2.4.3.tar.gz
shell>tar xzf snort-2.4.3.tar.gz
shell>tar xzf root.tar.gz
shell>cp /usr/local/src/Snort-Clamav/snort-clamav/snort-2.4.3-clamonly.diff /usr/local/src/
shell>patch -p0 <>cd snort.2.4.3
shell>cp ./m4/libprelude.m4 /usr/local/share/aclocal/
shell>export AUTOCONF_VERSION=2.59
shell>export AUTOMAKE_VERSION=1.9
shell>autoreconf -f
shell>./configure --enable-clamav --with-clamav-includes=/usr/local/include --with-clamav-defdir=/var/clamav --prefix=/usr/local/snort-clamav
shell>make && make install
You should add the ClamAV preprocessor before http_inspect preprocessor in the snort configuration file, I have renamed my snort configuration to snort_clamav.conf to reflect it's changes.
Just add the line below which will inspect all the network stream that flow to client host,
preprocessor clamav: ports all, toclientonly, dbdir /var/clamav, file-descriptor-mode
You can start running snort by now,
shell>/usr/local/snort-clamav/bin/snort -c /usr/local/src/snort-2.4.3/etc/snort_clamav.conf -l /usr/local/src/snort-2.4.3/snort_log
If you are getting error where preprocessor clamAV not found, that most prolly is the cause of you haven't do autoreconf -f or --enable-clamav when compiling Snort-ClamAV.
Hopefully this helps people who want to get Snort-ClamAV working on OpenBSD ;-)