If you snort user, and you like to stay cutting edge, bleeding-snort is what you suppose to try. Bleeding-snort offers the latest snort rule vs exploits/intrusions detected to date, it is double edged sword as at the same time it delivers the latest snort ruleset , it does offer you false positive as well since the ruleset is not tested heavily when outbreak period. However we would rather getting false positive instead of missing the detection of attacks when risk is out there somewhere since disabling snort rule never require a rocket scientist :P. Another thing I like about bleeding snort is that it does offer few interesting projects that related to snort which you can play around and implement depends on your network architecture and needs.
Okay, back to bleeding snort rules testing, I downloaded the latest bleeding snort rules from here, untar it to rules directory, and quickly add it to snort.conf. Since my intension is testing the wmf exploits, I decided to run metasploit msfweb to upload the exploit to port 8080. Then on the snort sensor host, I just run the command below,
On the other hand, I just use tcpdump to capture full content traffics,
shell>tcpdump -qeXX -tttt -n -s 1550 -w /nsm/full_trace.pcap &
Then I tail the alert log to view attacks in real time,
shell>tail -f /usr/local/src/snort-2.4.3/snort_log/alert
Okay, back to bleeding snort rules testing, I downloaded the latest bleeding snort rules from here, untar it to rules directory, and quickly add it to snort.conf. Since my intension is testing the wmf exploits, I decided to run metasploit msfweb to upload the exploit to port 8080. Then on the snort sensor host, I just run the command below,
shell>/usr/local/bin/snort -c /usr/local/src/snort-2.4.3/etc/snort.conf -l /usr/local/src/snort-2.4.3/snort_log -D
On the other hand, I just use tcpdump to capture full content traffics,
shell>tcpdump -qeXX -tttt -n -s 1550 -w /nsm/full_trace.pcap &
Then I tail the alert log to view attacks in real time,
shell>tail -f /usr/local/src/snort-2.4.3/snort_log/alert
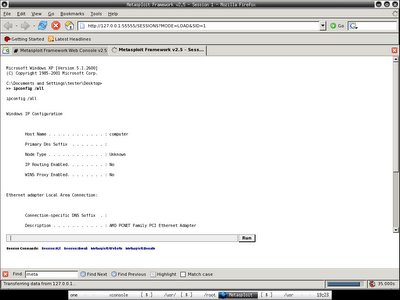
 Msfweb is running and waiting for connections to http://192.168.0.233:8080, and you may notice session 1 started ... someone was exploited!!!
Msfweb is running and waiting for connections to http://192.168.0.233:8080, and you may notice session 1 started ... someone was exploited!!! There are connections from the victims, the first connection is not gzip-encoded, the rest are gzip-encoded.
There are connections from the victims, the first connection is not gzip-encoded, the rest are gzip-encoded. Back to the sensor that running snort with bleeding snort rule loaded, I smell something bad when I tail the alert file, then I load the fishy pcap file that it captures in /usr/local/src/snort-2.4.3/snort_log to ethereal, apparently it is just showing the single packet that successfully exploiting the vulnerable victim which is not gzip encoded when I try to run wget http://192.168.0.233:8080, the rest of it I just connect to http://192.168.0.233:8080 with different kind of web browsers including lynx as victims.
Back to the sensor that running snort with bleeding snort rule loaded, I smell something bad when I tail the alert file, then I load the fishy pcap file that it captures in /usr/local/src/snort-2.4.3/snort_log to ethereal, apparently it is just showing the single packet that successfully exploiting the vulnerable victim which is not gzip encoded when I try to run wget http://192.168.0.233:8080, the rest of it I just connect to http://192.168.0.233:8080 with different kind of web browsers including lynx as victims. You should see the matching snort rule with the SID of 2002742 and the payload in ethereal. However do you really see the whole session of where the bad guys executing commands in your vulnerable host? That's where full content traffic data comes in hand when performing network forensic.
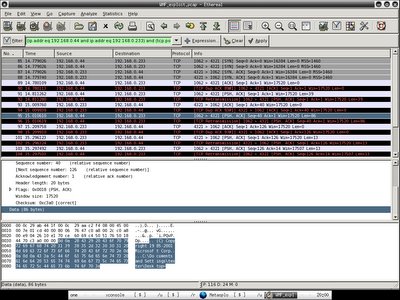
You should see the matching snort rule with the SID of 2002742 and the payload in ethereal. However do you really see the whole session of where the bad guys executing commands in your vulnerable host? That's where full content traffic data comes in hand when performing network forensic. Immediately I load the tcpdump log - full_trace.pcap to ethereal. Since I have snort rule detects that the src ip is 192.168.0.233 and the destination ip is 192.168.0.50(refer to screenshot 5), I can easily query it with the expression of ip.addr eq 192.168.0.233 and ip.addr eq 192.168.0.50 to trace the session between these two hosts.
Immediately I load the tcpdump log - full_trace.pcap to ethereal. Since I have snort rule detects that the src ip is 192.168.0.233 and the destination ip is 192.168.0.50(refer to screenshot 5), I can easily query it with the expression of ip.addr eq 192.168.0.233 and ip.addr eq 192.168.0.50 to trace the session between these two hosts. When I try to follow tcp stream to generate the transcript, everything is pretty obvious. You should understand perfectly what is happening and planning for countermeasure now.
When I try to follow tcp stream to generate the transcript, everything is pretty obvious. You should understand perfectly what is happening and planning for countermeasure now.Apparently we can alway do more with less, the whole process requires more efforts and lacking of efficiencies. That's where Network Security Monitoring(NSM) comes into the place, if you have NSM model deployed, it wouldn't take that hard to perform incident response and handling or even network forensic, that's why NSM requires the interaction of security analyst.
Network Security Monitoring(NSM) is the model that not only relies totally on the capabilities of Intrusion Detection System but a complete framework that utilizes the capabilities of security analyst, it is a must for the security analyst to fully understand what is happenning in the network as well as performing network forensic and investigation perfectly.
Network Security Monitoring(NSM) is the model that not only relies totally on the capabilities of Intrusion Detection System but a complete framework that utilizes the capabilities of security analyst, it is a must for the security analyst to fully understand what is happenning in the network as well as performing network forensic and investigation perfectly.

2 comments:
That day I installed my XP also using name Tester ;)
btw, Windows just released the patch, I wonder when others will discover another big hole ;)
btw again, cool one, gonna download and test, but, any manual to refer ;)
That was very rational. When deciding to put up security cameras, determine first the areas you’d like monitored. This gadget could be quite expensive if you’d put up one unit in every corner of the house. The key to such problem is proper angling. Home safety is paramount, that’s why it is really good news that home security cams are more affordable now. Having a secure home wouldn’t then be at all impossible for some people.
Alarm Monitoringep
Post a Comment