When I check on the ClamAV site today, it seems there is already signature for WMF exploits, I quickly install it through OpenBSD port and would like to give it a try since I'm thinking of trying on Snort+Clamav that available in bleeding as well.
Installing ClamAV via port,
shell>cd /usr/ports/security/clamav; make install
It will add a user _clamav automatically, then you have to configure the clamd.conf and freshclam.conf manually. Just copy the default one to /etc.
shell>cp /usr/local/share/examples/clamav/clamd.conf /etc
shell>cp /usr/local/share/examples/clamav/freshclam.conf /etc
You should be able to figure out how to configure it properly with this doc.
After you have configured it, I suggest you run freshclam to update the signature database first since you don't have main.cvd and daily.cvd initially.
I quickly scan /root/WMF by using clamscan, and apparently it works perfectly. You may see the result below.
Installing ClamAV via port,
shell>cd /usr/ports/security/clamav; make install
It will add a user _clamav automatically, then you have to configure the clamd.conf and freshclam.conf manually. Just copy the default one to /etc.
shell>cp /usr/local/share/examples/clamav/clamd.conf /etc
shell>cp /usr/local/share/examples/clamav/freshclam.conf /etc
You should be able to figure out how to configure it properly with this doc.
After you have configured it, I suggest you run freshclam to update the signature database first since you don't have main.cvd and daily.cvd initially.
I quickly scan /root/WMF by using clamscan, and apparently it works perfectly. You may see the result below.
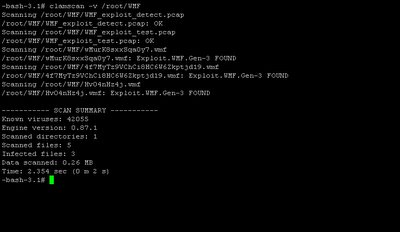
Why use commercial AV when there's effective and cool one available??!!!
3 comments:
I bet there are times when there are signatures that clamav misses and you never report it.
I think you haven't get my point of which every single Antivirus vendor always has their advance and lacking features, it is just that we can make a clever choice from all the alternatives. By the way, don't tell me you able to find Antivirus vendor that is bulletproof.
Use my product please, I can free you 2 years trial ;) Just send me an email...
Post a Comment