Systrace serving as host IDS/IPS for OpenBSD to monitor all the executables, it monitors and controls an application's access to the system by enforcing access policies for system calls. Using it might help to quarantine the bug of 3rd part applications that either install through packages/ports or source when we deploy it's access policies. Not only we can use it to protect the system but at the same time we can use it to trace the behaviour and functions that performed by untrusted executables in the system.
So how can systrace actually can help us to understand suspicious and untrusted executable file. I used the script that been uploaded by the hacker a while ago as an example which is actually a synner.pl perl script that can be downloaded from securiteam.com. I have renamed back the script so that it is identical to me.
In order to know what this executable file doing without even looking at the source code, I quickly generate systrace policy file for it.
shell>systrace -A /root/synner.pl
Use ./synner.pl
So how can systrace actually can help us to understand suspicious and untrusted executable file. I used the script that been uploaded by the hacker a while ago as an example which is actually a synner.pl perl script that can be downloaded from securiteam.com. I have renamed back the script so that it is identical to me.
In order to know what this executable file doing without even looking at the source code, I quickly generate systrace policy file for it.
shell>systrace -A /root/synner.pl
Use ./synner.pl

To know how the executable file actually works, I run it with the sandbox of systrace by running
shell>systrace -d /root/.systrace /root/synner.pl 192.168.0.140 22 10000
shell>systrace -d /root/.systrace /root/synner.pl 192.168.0.140 22 10000
Systrace -d /root/.systrace means using the policy files in the directory /root/.systrace, this is useful if you have multiple policy files in the directory. If you just want to monitor single application per policy file, you can just go with -f switch. The synner script will connect to port 22 of host 192.168.0.140 in 10000 seconds. From the script description, we know that it is the spoof-Dos tool, and with spoofing it means it might be randomize so that's where we have seen that it need to access to /dev/arandom from the root_synner_pl policy file. Xsystrace is popped up if any access to the certain function is not implicitly allowed in the policy file, from here we can monitor each command line switches or options that need to access or perform what functions which giving us more clear view of the executable files. So here we can see that it need to access to /etc/resolv.conf, that might be used to resolve the hostname.
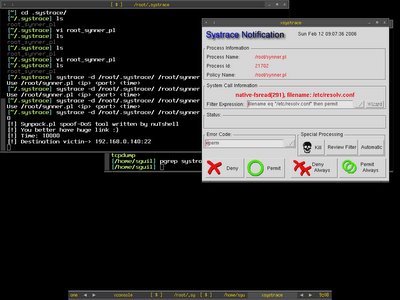
Then here we found out that it needs to perform function socket which create an end point for communication that uses AF_INET - address family IP v4 and raw socket. I click on permit to see how it goes next.
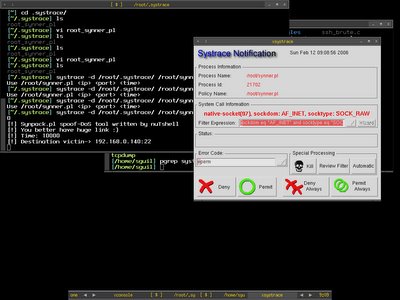
There we see it perform sendto function which means now it is in connected state and transmitting message to another socket.
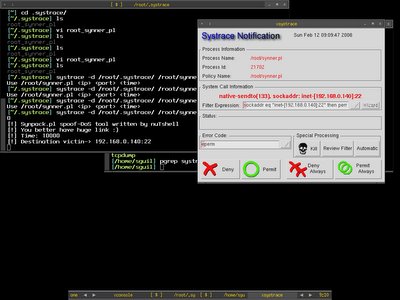
After I keep repeating permit the same functions because it keeps doing the same thing, therefore I just click on Permit Always button to get it finished automatically. Now I have already known what is the executable file doing without even looking at the source code.
Systrace is very flexible that not only it serves as application monitoring and controlling tool but as well as a decent analyze tool. It saves time of SysAdmin to analyze the third party applications to avoid backdoor or malicious function that running on the system by hand especially to someone not a decent coder like me. I would love to learn more about it since I get to learn OpenBSD function at the same time when I dig on it.
I have always like to learn more about the native and built-in tool for OpenBSD.
Systrace is very flexible that not only it serves as application monitoring and controlling tool but as well as a decent analyze tool. It saves time of SysAdmin to analyze the third party applications to avoid backdoor or malicious function that running on the system by hand especially to someone not a decent coder like me. I would love to learn more about it since I get to learn OpenBSD function at the same time when I dig on it.
I have always like to learn more about the native and built-in tool for OpenBSD.
Peace :]
No comments:
Post a Comment