While analyzing the behaviour of brontok using Process Explorer, it is trying to perform denial of service with ping flood. It is trying to run the command - ping 17tahun.com -n 250 -l 747. Why it ping with the payload of 747 bytes, may he or she is a lover of boeing airplane 747? The airstrike seems successful since I can't browse 17tahun.com with my browser.
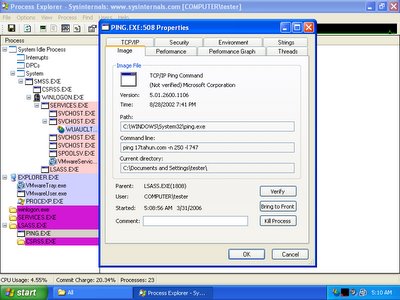
Once brontok goes wild, it will try to spawn more pings in order to bring down 17tahun.com.
You may like to view this interesting graph.
However what funny is when I tried to ping 17tahun.com manually, I get a very surprised result - 64 bytes from 127.0.0.1, it is supposed to be destination host unreachable or maybe request timed out if the destination host is down. But what tends to shock me is it replied with the lookpback address - 127.0.0.1.

I ran into dnsreport.com and checking it's dns status, and I found this interesting piece of it's result.
Your www.17tahun.com A record is
www.17tahun.com. A 127.0.0.1 [TTL=3601] [*L]

It seems that the DNS record is totally incorrect, I'm now having doubt on this, is this something to do with DNS cache poisonning?
Enjoy .....
P/S: Brontok tries to bring down other sites by ping flooding as well, however those are not as interesting as this one.
Enjoy .....
P/S: Brontok tries to bring down other sites by ping flooding as well, however those are not as interesting as this one.
2 comments:
This isn't entirely unheard of... I seem to remember microsoft changing the DNS record of one of their servers in response to a DDoS from a virus in the past. If you're paying per megabyte bandwidth charges and don't have a fast enough server/link to weather the DoS anyway then deflecting it elsewhere makes some sense. If your site's going to be unreachable anyway you may as well at least avoid the massive bandwidth bill.
Maybe deflecting is the way when there's no countermeasure, however I think it should not be too trivial to encounter ping flooding if ISP involves. Nice comment anyway :)
Post a Comment