I haven't been writing anything regarding NSM tools recently, and yes I'm actually writing and editing my handbook indeed. Here's another interesting tool to monitor and track what is happenning in your network.
While tools like iftop, bwm-ng can provide you the clear view of your network interface statistic, tcptrack takes it further by allowing you to monitor the network by specifying bpf like filter. It can provide quick view when you suspect that your network is being hacked or having malicious events running. The only weak point about tcptrack as is name implied, it doesn't track icmp and udp based connection, thus you can't get overview of the whole network activities that happening in the network. I install tcptrack via FreeBSD port/package since it is the easiest way to get it install, and I just need to run,
While tools like iftop, bwm-ng can provide you the clear view of your network interface statistic, tcptrack takes it further by allowing you to monitor the network by specifying bpf like filter. It can provide quick view when you suspect that your network is being hacked or having malicious events running. The only weak point about tcptrack as is name implied, it doesn't track icmp and udp based connection, thus you can't get overview of the whole network activities that happening in the network. I install tcptrack via FreeBSD port/package since it is the easiest way to get it install, and I just need to run,
shell>tcptrack -i fxp0 -r 10
It will start to sniff on fxp0 interface and with -r 10, it will refresh the screen so that close connection won't be shown anymore as it is meaningless. You may notice that it shows total connection at the footer. You can pause it and sort it with p and s key.
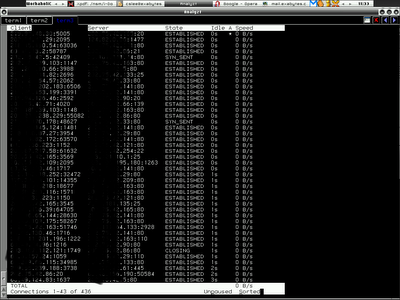
If you just want to navigate the connection that belonged to 10.0.0.1 alone, you can run -
shell>tcptrack -i fxp0 -r 10 src or dst 10.0.0.1
You can also checking whether your server - 192.168.0.100 is connecting to non-legitimate smtp server by specifying -
shell>tcptrack -i fxp0 -r 10 src 192.168.0.100 \
and dst port 25
While you are suspecting your network is infected by worms such as sasser, korgo that will launch outbound connections to port 445 that exploiting lsass. You can actually run this command to check on the outbound traffics from your network, for example let's say your network is 192.168.5.0/24. Just run -
shell>tcptrack -i fxp0 -r 10 src net 192.168.5 and dst port 445
Screenshot below shows the output -
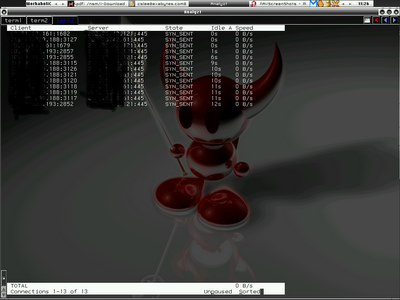
Interesting huh, let's have fun with tcptrack.
Peace (:])
2 comments:
just got it from the ports, great monitoring tool, thanks!
Have fun !!!!!
Post a Comment