That was two years back when I started using honeyd for my own research and stop after version 0.8, it's time to revisit the honeyd since v1.0 sounds mature enough :], and I would like to see the differences of it compared to previous version. The obvious changes would be arpd no longer needed and dhcp is supported, honeyd has it's own management console and even though it's not in mature stage, however it would be kind of useful especially you can easily troubleshoot your setup with it. Hereby I will demonstrate a simple setup of honeyd on OpenBSD, and testing it using Scapy and Nmap.
First add this two line in your /root/.profile
PKG_PATH=ftp://ftp.openbsd.org/pub/OpenBSD/3.8/packages/i386/
export PKG_PATH
Installing Honeyd package
shell>pkg_add ${PKG_PATH}honeyd-1.0p0.tgz
The installation itself will create a user _honeyd since it's not wise to run honeyd as root. Now you need to create two logs for the user _honeyd.
shell>cd /var/log
shell>touch honeyd.log honeyd_service.log; chown -R _honeyd:_honeyd honeyd.log honeyd_service.log
You can start the configuration of honeyd by now, I just configure a simple one that consists of two windows 2000 advanced servers and one cisco router. Below is my /etc/honeyd.conf file.
###################################
create windows
set windows personality "Microsoft Windows NT 4.0 Server SP5-SP6"
#set windows uptime 123456
set windows maxfds 35
add windows tcp port 80 "sh /usr/local/share/honeyd/scripts/web.sh"
add windows tcp port 139 open
add windows tcp port 137 open
add windows udp port 137 open
add windows udp port 135 open
set windows default tcp action reset
set windows default udp action reset
#dhcp windows on pcn0 ethernet "3com"
set windows ethernet "3com"
bind 192.168.0.135 windows
bind 192.168.0.136 windows
create router
set router personality "Cisco 1601R router running IOS 12.1(5)"
set router default tcp action reset
add router tcp port 22 "/usr/local/share/honeyd/scripts/test.sh"
add router tcp port 23 "/usr/local/share/honeyd/scripts/router-telnet.pl"
set router ethernet "cisco"
bind 192.168.0.160 router
####################################
One of the thing worth to be mentionned is that you are now able to spoof the MAC address of the certain vendors like cisco, 3com and etc. This is rather good to avoid the detection of virtual honeypot since most properly Cisco Router would use their own Cisco NIC. Take note of the bold line above.
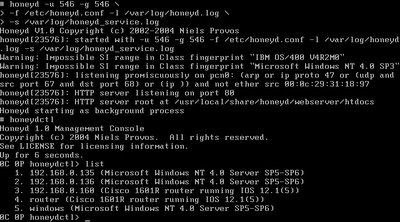
We can now start running honeyd by using the commands in the screenshot. By using honeydctl(honeyd management console), we can list out our virtual honeypots, 192.168.0.135 and 192.168.0.136 are my simulated windows servers and 192.168.0.160 is my simulated cisco router.
First add this two line in your /root/.profile
PKG_PATH=ftp://ftp.openbsd.org/pub/OpenBSD/3.8/packages/i386/
export PKG_PATH
Installing Honeyd package
shell>pkg_add ${PKG_PATH}honeyd-1.0p0.tgz
The installation itself will create a user _honeyd since it's not wise to run honeyd as root. Now you need to create two logs for the user _honeyd.
shell>cd /var/log
shell>touch honeyd.log honeyd_service.log; chown -R _honeyd:_honeyd honeyd.log honeyd_service.log
You can start the configuration of honeyd by now, I just configure a simple one that consists of two windows 2000 advanced servers and one cisco router. Below is my /etc/honeyd.conf file.
###################################
create windows
set windows personality "Microsoft Windows NT 4.0 Server SP5-SP6"
#set windows uptime 123456
set windows maxfds 35
add windows tcp port 80 "sh /usr/local/share/honeyd/scripts/web.sh"
add windows tcp port 139 open
add windows tcp port 137 open
add windows udp port 137 open
add windows udp port 135 open
set windows default tcp action reset
set windows default udp action reset
#dhcp windows on pcn0 ethernet "3com"
set windows ethernet "3com"
bind 192.168.0.135 windows
bind 192.168.0.136 windows
create router
set router personality "Cisco 1601R router running IOS 12.1(5)"
set router default tcp action reset
add router tcp port 22 "/usr/local/share/honeyd/scripts/test.sh"
add router tcp port 23 "/usr/local/share/honeyd/scripts/router-telnet.pl"
set router ethernet "cisco"
bind 192.168.0.160 router
####################################
One of the thing worth to be mentionned is that you are now able to spoof the MAC address of the certain vendors like cisco, 3com and etc. This is rather good to avoid the detection of virtual honeypot since most properly Cisco Router would use their own Cisco NIC. Take note of the bold line above.
We can now start running honeyd by using the commands in the screenshot. By using honeydctl(honeyd management console), we can list out our virtual honeypots, 192.168.0.135 and 192.168.0.136 are my simulated windows servers and 192.168.0.160 is my simulated cisco router.
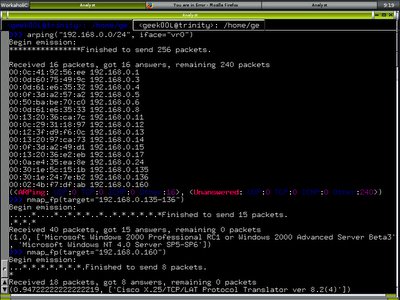
To test against whether the honeyd is setup properly, I launch up Scapy, using arping and nmap_fp to fingerprint it.
Apparently the result is matching my setup, let's see how about running testing by using native Nmap. There are two screenshots below, the first one is running nmap against Windows box and the second one is against the Cisco router.

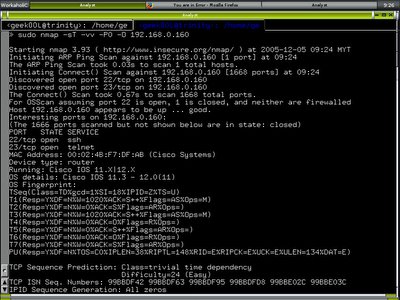
If you look at it closely, you might see the Mac Address belongs to the vendors I specified in the honeyd config file, windows box using 3com Nic and Cisco router using it's own NIC :]
To monitor who is connecting to the virtual honeypot in real time.
shell>tail -f /var/log/honeyd.log
To stop all the honeyd process.
shell>kill -9 `pgrep honeyd`
We have seen improvment in honeyd so far, and what I noticed in the TODO file from the honeyd source tarball is that some simulated operating system don't support defragmentation, maybe OpenBSD PF scrub function might do the trick for it, and I can't wait for the function of start, shutdown and reboot simulated OS by using honeyd management console.
Honeyd becomes least popular for honeypot setup in the real world and the one that take over would be the next generation honeypot such as mwcollect and nepenthes. Both are more close to the malware collection honeypot. Honeyd simulating the OS level is not attractive enough for the malicious users nowadays, on the other hand mwcollect and nepenthes simulating the vulnerable applications would be more attrative to the bad guy.
Enjoy.
To monitor who is connecting to the virtual honeypot in real time.
shell>tail -f /var/log/honeyd.log
To stop all the honeyd process.
shell>kill -9 `pgrep honeyd`
We have seen improvment in honeyd so far, and what I noticed in the TODO file from the honeyd source tarball is that some simulated operating system don't support defragmentation, maybe OpenBSD PF scrub function might do the trick for it, and I can't wait for the function of start, shutdown and reboot simulated OS by using honeyd management console.
Honeyd becomes least popular for honeypot setup in the real world and the one that take over would be the next generation honeypot such as mwcollect and nepenthes. Both are more close to the malware collection honeypot. Honeyd simulating the OS level is not attractive enough for the malicious users nowadays, on the other hand mwcollect and nepenthes simulating the vulnerable applications would be more attrative to the bad guy.
Enjoy.
1 comment:
i tried to setup honeyd on ubuntu hardy after read your blog. But my honeyd doesn't log anything even after i run a port scanner. I used honeyd.conf same as in your blog. Can you guide me? I just want to try this kind of thing
Post a Comment