I have read the taosecurity blog and the post regarding Snort BO exploit is kinda interesting, Kyle Haugness has written a tool to detect the Snort BO exploit and he recommends using netdude and tcpreplay to edit and replay the pcap file that provided by him. Let's see how we can do it by using these two tools.
Download the pcap from Kyle's site.
shell>wget http://handlers.dshield.org/khaugsness/1025a
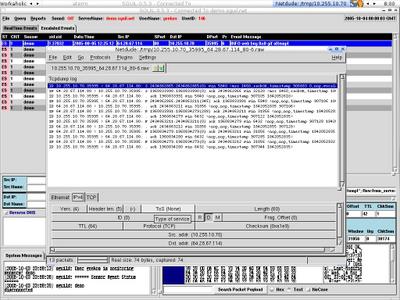
Then load the pcap file to netdude.
Download the pcap from Kyle's site.
shell>wget http://handlers.dshield.org/khaugsness/1025a
Then load the pcap file to netdude.

Now change the ip and mac address by just double clicking the header field. I assume source ip is 192.168.0.44 and destination ip is 192.168.0.66.

After you have modified it, save it and you can now replay the pcap file. As I save the file as snortBO1025a.cap, we can now replay the pcap file by enter the command below.
shell>tcpreplay -i bge0 snortBO1025a.cap
sending on:bge0
1 packets (1086 bytes) sent in 0.68 seconds
157528.3 bytes/sec 1.20 megabits/sec 145 packets/sec
Here's the result shows in ethereal, it seems work and I have sent 8 packets.

The payloads below show the replies from the host 192.168.0.66

Tcpreplay is nifty tool to replay the traffic, however I'm using the old 2.2 version which is in freeBSD port, the latest should be version 3 which is more powerful and I will try it if I have time in hand.
Netdude is the easiet tool I find so far for packet modification purpose, of course it is nothing hard to do with packet forging as well when you able to modify the header of packets. For ethereal, one really good point that I give thumbs up for it is that the capability of differenatiate normal and malformed packet. This is definitely saving the valuable time of analyst in handling incident response and network forensics :)
For people who fall in love with Packet Monkeying, go SCAPY!!!!!
Netdude is the easiet tool I find so far for packet modification purpose, of course it is nothing hard to do with packet forging as well when you able to modify the header of packets. For ethereal, one really good point that I give thumbs up for it is that the capability of differenatiate normal and malformed packet. This is definitely saving the valuable time of analyst in handling incident response and network forensics :)
For people who fall in love with Packet Monkeying, go SCAPY!!!!!