The company I work with utilizing ticket based system, yet this is effective way to manage and handle customers since it is more interactive comparing to using email system alone. However this time, it is used by the hacker to try to perform social engineering to get around the firewall and compromising the network without much efforts.
Normally we allow customers to send attachment especially when they need to send screenshots such as ping or traceroute result. That may help to identify and fix client's issue. But allowing attachment seems not a good idea this time. The hacker was trying to trick the service support to open the attachment by sending this look so "INNOCENT" attachment.
Normally we allow customers to send attachment especially when they need to send screenshots such as ping or traceroute result. That may help to identify and fix client's issue. But allowing attachment seems not a good idea this time. The hacker was trying to trick the service support to open the attachment by sending this look so "INNOCENT" attachment.
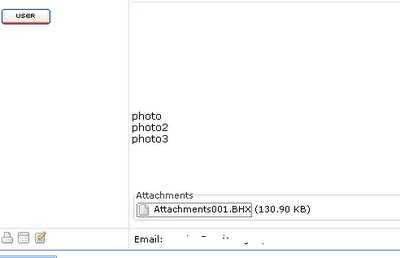
I downloaded the attachment, and what starts to make me feel suspicious would be the attachment name is index.php after downloading it instead of the one shown in the ticket, this doesn't match at all. To identify the file type, I run the file command, and the file is uuencoded, if you don't know what is uuencoding, check the link here. Most to most it is unix to unix encoding and very popular in sending binary through email attachment these days.
I just decode it with uudecode that is installed by default in most of unix-like system, I redirect the output to fake after decoding. I recheck the filetype and apparently it is MS DOS executable.
I just decode it with uudecode that is installed by default in most of unix-like system, I redirect the output to fake after decoding. I recheck the filetype and apparently it is MS DOS executable.
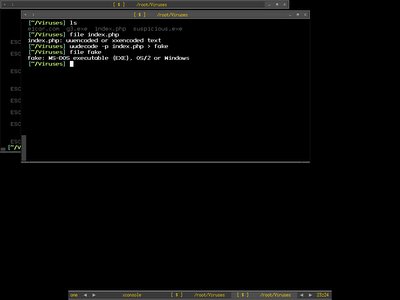
I tried to run strings against the file, and it showed some clues to me what this file is all about especially this string - Exploite ...
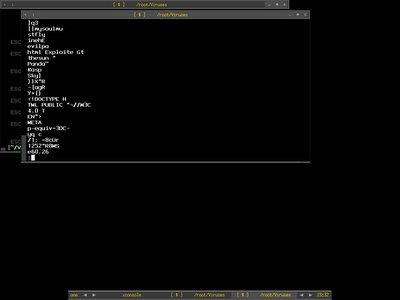
Walking down the strings, we can already guess what this executable file trying to do, though port 80 for sure is good port to bypass firewall since most firewall implementation won't block inbound or outbound http. That may makes a good and stealthy backdoor indeed.
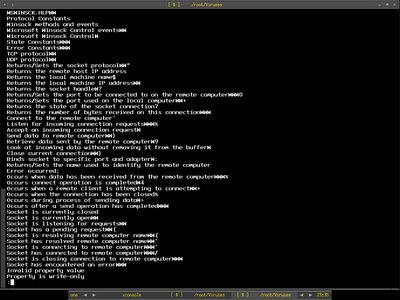
Sometimes it is not too hard to compromise enteprise network if you play around with the social engineering tricks especially when people have no idea what they are doing. Even security policy enforcement won't help sometimes if users are not aware enough.
Living with threats everyday .....
Peace :]
1 comment:
Cool!
Post a Comment